Abusing Cloudflared - A Proxy Service To Host/Share Applications
About
I recently came across Cloudflared project. I have wrote previously on Visual Studio Code DevTunnels and how they can be misused to host phishing sites directly from your local machine over the internet.
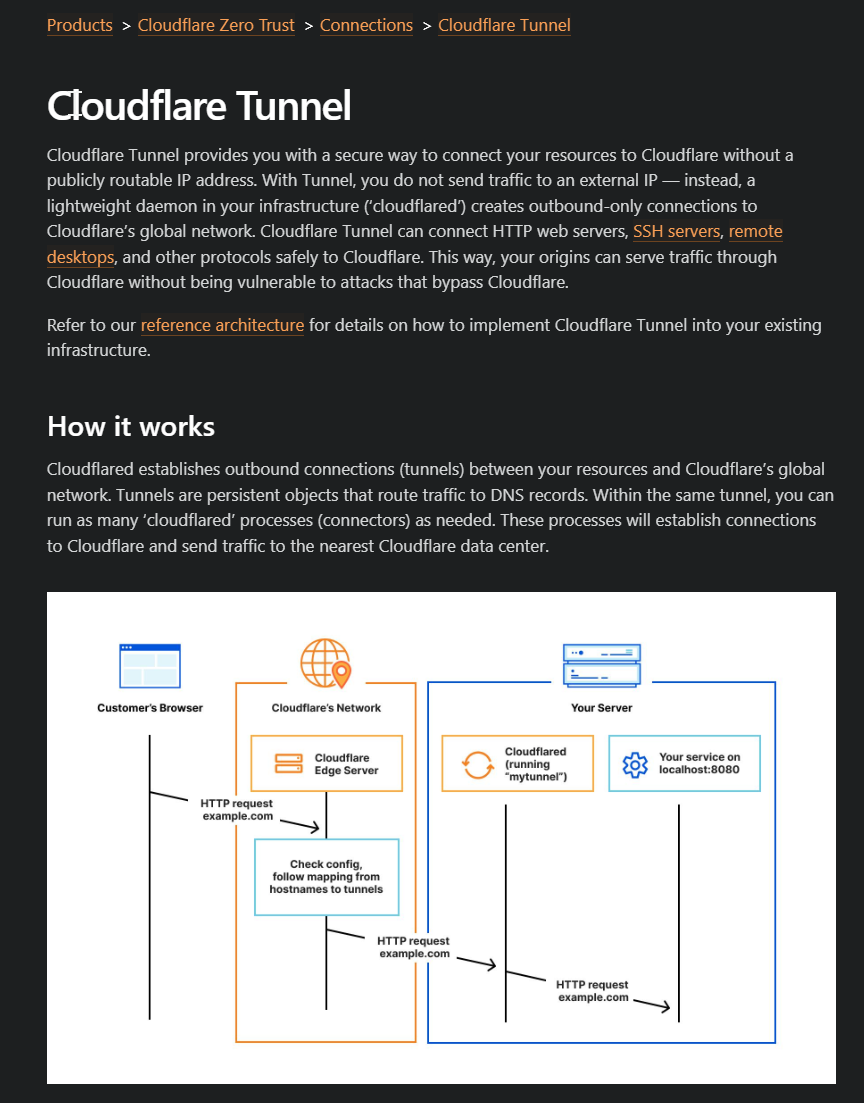
The above screenshot mentions all about the reason and how to use CloudFlare Tunnel and the below URL will provide all the documentations around the same.
https://developers.cloudflare.com/cloudflare-one/connections/connect-networks/
However, this looks to be another binary via which we can achieve the same. The major problem which i see is that you can create tunnels unauthenticated, thus giving it into the hands of the user on how they actually want to use this functionality.
Testing
I simply downloaded the tool onto my Windows Operating System.
Then simply run the below command to create the tunnels.
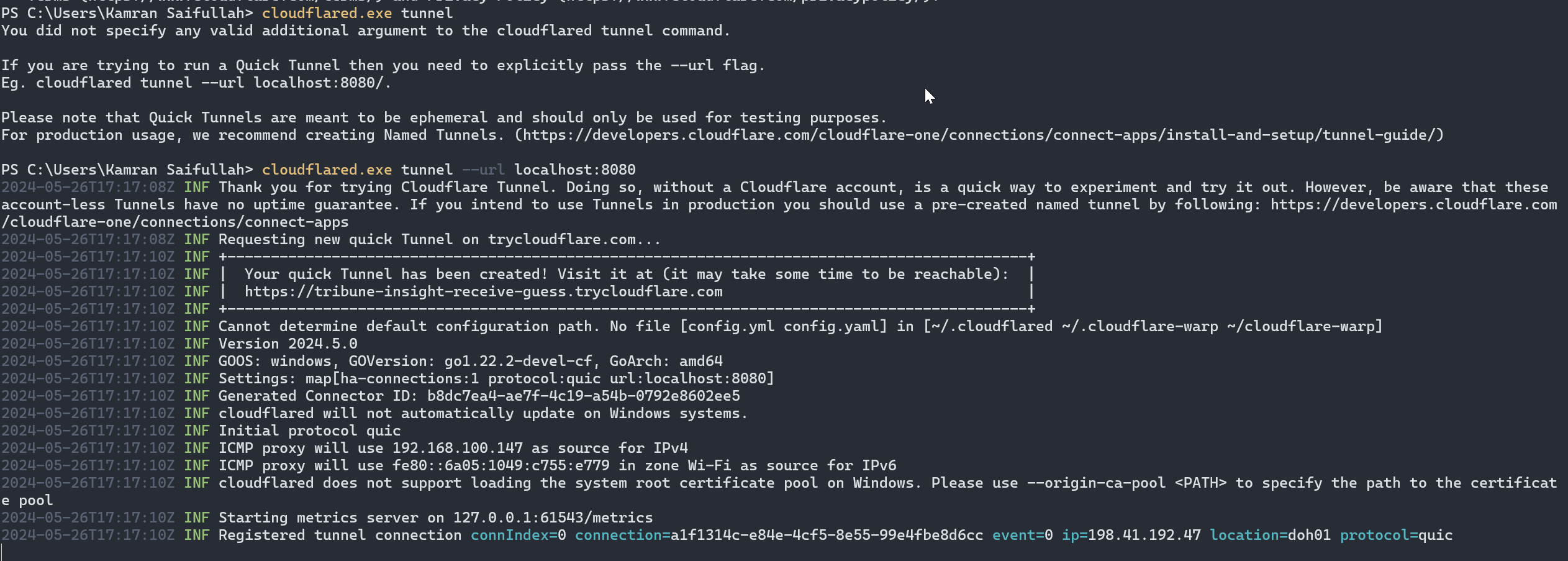
Once we have this up and running we can simply, use the URL generated for us and we can access it over the internet.
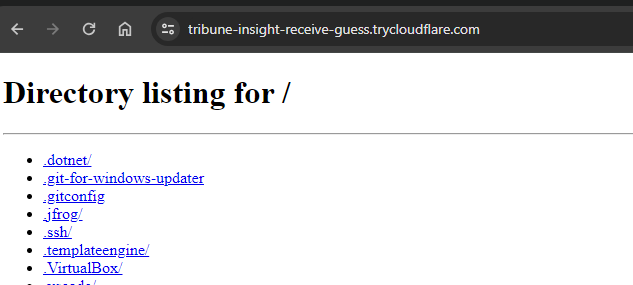
There are tons of decent usecases for using this functioanlity, however without proper training and controls around this, this is going to create a a mess.
Adversaries will start using this to have a secure way into getting into the environements. Though, it is dependent on the usecases and how the security controls are implemented.
Phishing Simulation
I have been able to run a Phishing Campaign hosted directly on my local machine over the internet and getting back all the results on my machine.
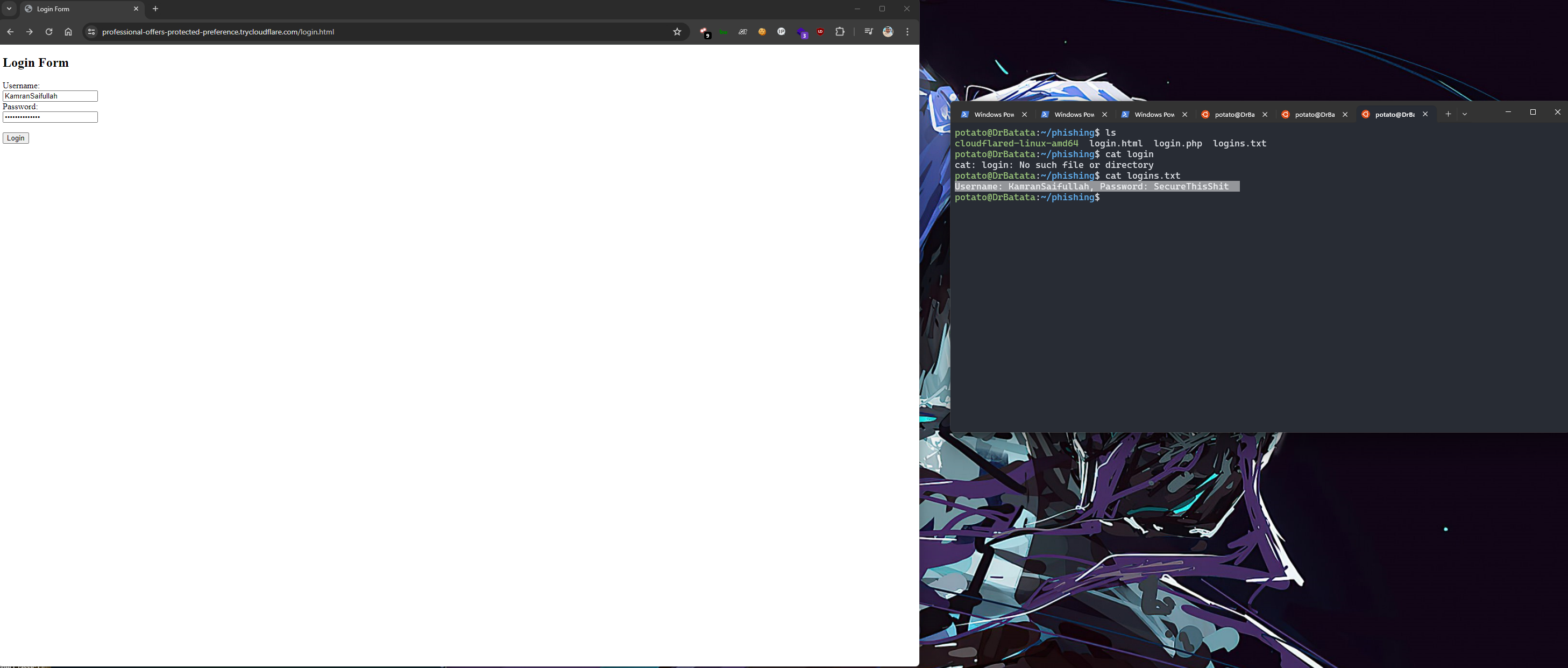
We can clearly see that by simply hosting a PHP site locally we can have it exposed over the internet and we can connect to it securely.
Similarly, adversaries will be able to host their payloads and have them accessed through victims machines and a way to deliver their payloads.
As this is official domain from CloudFlare this will not be blocked straight away, additional controls are monitoring is required to ensure these domains are properly monitored as its fairly easy for the developers to have this tool installed and have data exfiltrated directly over the internet when there are strict controls around.
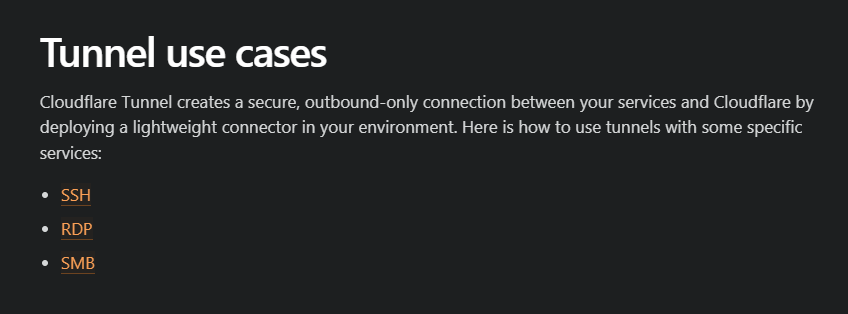
So, we are not just talking about hosting Phishing Sites, but we can also use this for SSH, RDP and SMB respectively. I am sure there are going to be more usecases with this as well.
Google Dorking
Similarly a quick Google Search using the site:.trycloudflare.com DORK reveals a number of apps which are exposed by the users respectively.
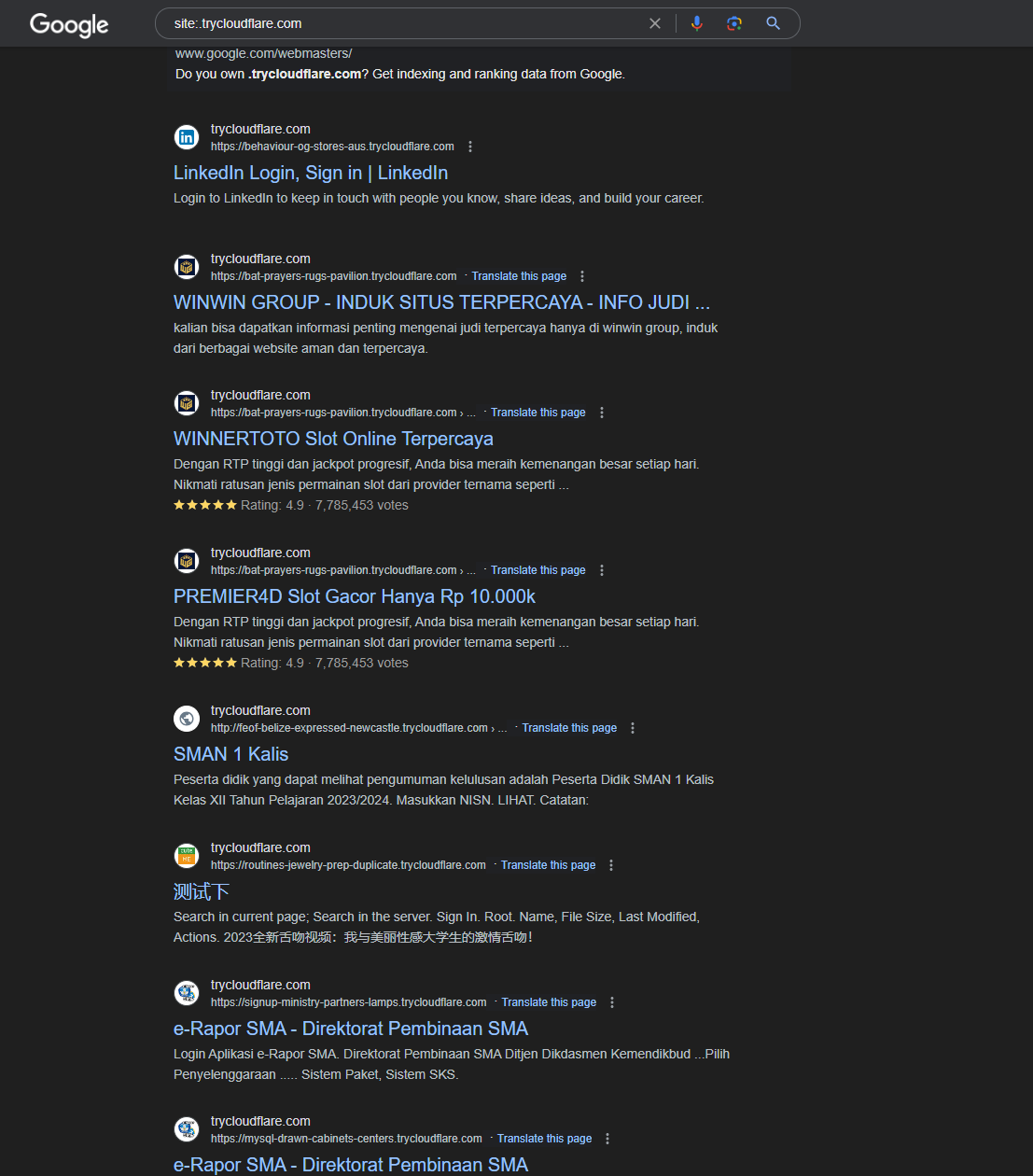
URLScan Results
Similarly, as the tool has been fairly old in the market but have been renamed. We can check URLSCAN.IO for the results.
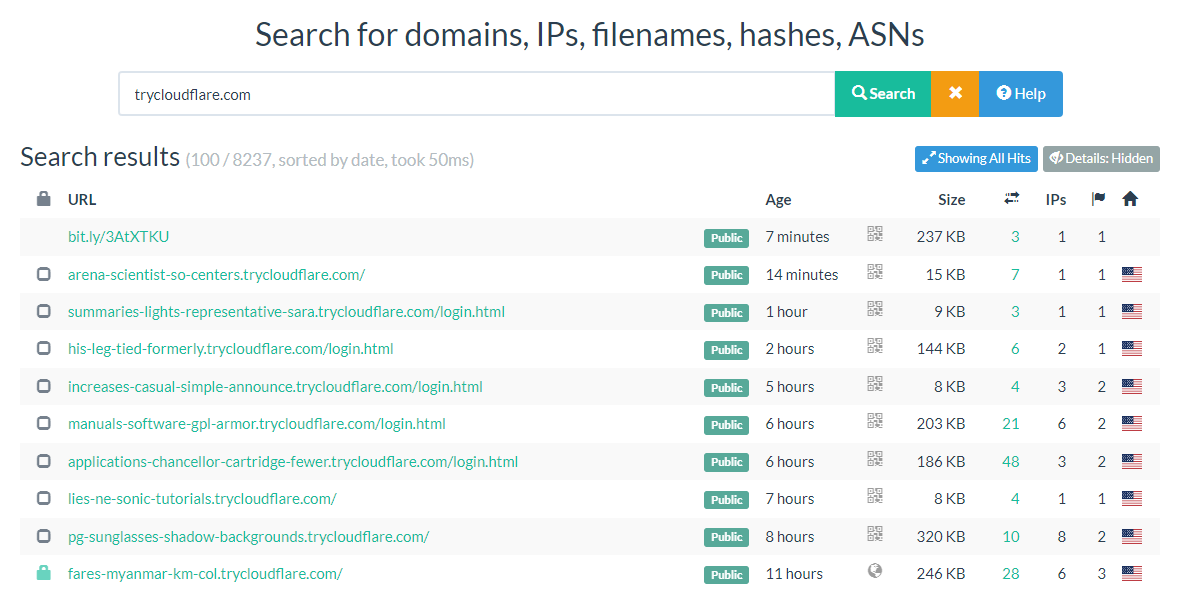
In total 8000+ domains have been scanned and checked on the URLSCAN.IO.
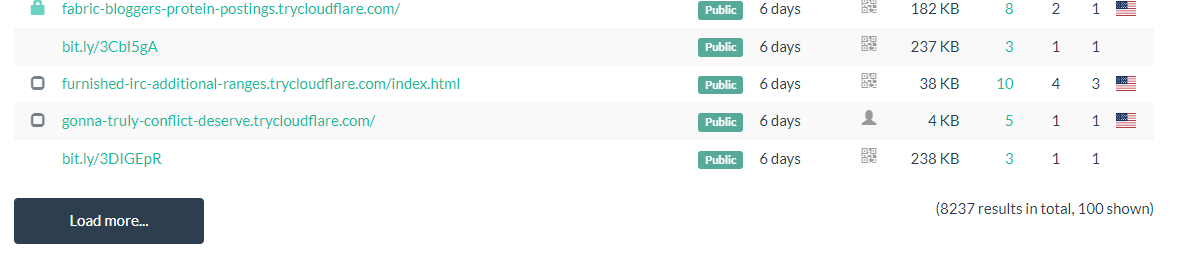
This proves that this has been used extensively in the market and definitely some of the domains are actually phishing domains.
SigmaHQ Contribution
I have created a Sigma Rule for the same and PR has been merged into the main SigmaHQ repository. Same can be used for detection as it includes other URLs which are related to the same functionality.
https://github.com/SigmaHQ/sigma/pull/4863